Following is an inventory of essentially the most regularly requested Cyber Security interview questions and solutions.
1) What’s Cyber Security? / What are you aware about Cyber Security?
Cyber Security is the apply of defending internet-connected programs akin to {hardware}, program, packages, computer systems, servers, cell gadgets, digital programs, networks, and information from malicious digital assaults. The principle objective of cyber safety is to guard in opposition to cyberattacks like accessing, altering, or destroying delicate data out of your pc system.
Cyber attackers are primarily geared toward accessing, altering, or destroying delicate data, extorting cash from customers, or interrupting regular enterprise processes. Cyber Security is also referred to as pc safety, data know-how (IT) safety, cybersecurity, and so on. It’s used to measure the fight threats in opposition to networked programs and purposes, whether or not these threats originate from inside or exterior of a corporation.
We are able to divide the time period cyber safety into two elements: cyber and safety. Cyber refers back to the know-how that features programs, networks, packages, and information of an internet-connected system. The phrase safety specifies the safety of programs, networks, purposes, and data.
2) What’s Cyber Crime? Give some examples of Cyber Crime.
Cyber Crime is rather like common crime however occurs on the Web. Following are some examples of Cyber Crime:
- Id Theft
- On-line Predators
- Hacking of delicate data from the Web
- BEC (“Enterprise E mail Compromise”)
- Ransomware
- Stealing mental property
3) Why is Cyber Crime growing daily yearly?
Cyber Crime is growing daily yearly due to the next causes:
- Cyber Crime is simple to perform. An individual having good information of pc hacking can do Cybercrime.
- There’s a decrease threat of getting caught in Cybercrime.
- A cyber attackers can get big cash for his or her little work.
- Cyber attackers can goal 1000’s of victims.
- With the introduction of cryptocurrencies, cash laundering is getting simpler.
4) What’s the essential objective of Cyber Security?
The principle goal of cyber safety is to guard information from cyber-attacks. It follows a precept referred to as CIA trio. It’s a safety sector that gives a triangle of three linked ideas. The CIA mannequin is used to assist organizations to develop insurance policies for his or her data safety structure. There are three essential parts Confidentiality, Integrity, and Availability of this CIA mannequin. A number of of those ideas is damaged when it finds a safety breach. This mannequin supplies a safety paradigm to information people by way of many points of IT safety.
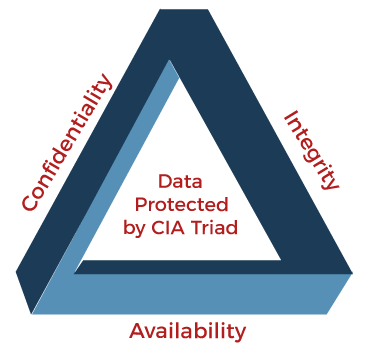
Let’s examine these three safety points intimately:
Confidentiality: Confidentiality is used to offer privateness to stop unauthorized entry to information. It ensures that the information is barely accessible to those that are approved to make use of it and restricts entry to others. It restricts important data to be uncovered to the improper fingers. A great instance of Confidentiality is Information encryption which is used to maintain data non-public.
Integrity: The Integrity precept is used to guarantee that the information is real, appropriate, and secure from undesirable risk actors or unintentional consumer alteration. It additionally specifies that the supply of knowledge have to be real. If any adjustments are made, precautions needs to be taken to guard delicate information from corruption or loss and get better from such an incident shortly.
Availability: The Availability precept ensures that the knowledge is consistently accessible and accessible to those that have entry to it. It additionally ensures that any sorts of system failures or cyber-attacks don’t impede these accesses.
5) What are the principle benefits of cyber safety?
Following is an inventory of essential benefits of cyber safety:
- Cyber safety protects on-line companies and transactions in opposition to ransomware, malware, on-line frauds, and phishing.
- It protects the end-users.
- It supplies nice safety for each information in addition to networks.
- It could improve the restoration time after a breach.
- It prevents unauthorized customers from accessing delicate data.
6) What’s the distinction between IDS and IPS?
An inventory of variations between IDS and IPS:
| IDS | IPS |
|---|---|
| IDS stands for Intrusion Detection Techniques. | IPS stands for Intrusion Prevention Techniques. |
| IDS can solely detect intrusions, however it’s unable to stop intrusions. | IPS can detect in addition to forestall intrusions. |
| IDS is a monitoring system. | IPS is a management system. |
| IDS requires a human or one other system to take a look at the outcomes. | IPS solely requires a often up to date database with the newest risk information. |
7) What are the important thing parts of Cyber Security?
Following is the checklist of key parts of Cyber Security:
- Info safety
- Community safety
- Operational safety
- Software safety
- Finish-user safety
- Enterprise continuity planning
8) What’s Cryptography?
Cryptography is a way or apply used to guard data from third events referred to as adversaries. It’s a technique of defending data and communications by way of codes in order that solely these for whom the knowledge is meant can learn and course of the information. In Cryptography, we additionally research a number of methods for safe communication, primarily to guard the delicate information from third events that the information is just not meant for.
9) What’s the distinction between a risk, vulnerability, and threat?
Usually, folks assume that risk, vulnerability, and threat are the identical, however there are some essential variations between them:
Menace: A risk will be any type of hazard able to destroying or stealing information, disrupting operations, or inflicting hurt usually. Some examples of threats are Malware, phishing, information breaches, and even unethical staff, and so on. Any kind of risk could also be dangerous to the group, so; it’s important to grasp threats for creating efficient mitigation and making knowledgeable cybersecurity selections.
Vulnerability: Vulnerability is a doable downside or a flaw in {hardware}, program, personnel, or procedures that may hurt the group. Menace actors can use these vulnerabilities to realize their targets.
Some examples of vulnerabilities are given beneath:
- Bodily vulnerabilities: Publicly uncovered networking gear is an instance of Bodily vulnerability.
- Program vulnerabilities: e. buffer overflow vulnerability in a browser.
- Human vulnerabilities: e. an worker weak to phishing assaults.
- Zero-day vulnerability: It’s a kind of vulnerability for which a treatment is just not but accessible.
To manage up with vulnerabilities, we’ve a way referred to as Vulnerability administration. It’s the technique of figuring out, reporting and repairing vulnerabilities.
Threat: Threat is a mixture of risk and vulnerability. After we mix the chance of a risk and the consequence of vulnerability, it’s referred to as a threat. Threat is the chance of a risk agent efficiently exploiting the vulnerability.
A method to calculate threat:
- Threat = chance of a risk * Vulnerability Influence
To manage and handle the chance, we use a way referred to as Threat administration. It’s a technique of figuring out all potential hazards, analyzing their influence, and figuring out the very best plan of action. That is an always-running process used to look at new threats and vulnerabilities often. Through the use of this technique, we will keep away from or decrease dangers. We are able to additionally settle for or handed them to a 3rd celebration in accordance with the response chosen.
10) What’s the distinction between Symmetric and Uneven Encryption in Cyber safety?
An inventory of variations between Symmetric and Uneven Encryption in Cyber safety:
| Comparability Index | Symmetric Encryption | Uneven Encryption |
|---|---|---|
| Encryption key- | Symmetric Encryption makes use of the identical key for Encryption & decryption. | Uneven Encryption makes use of completely different keys for Encryption & decryption. |
| Efficiency- | Efficiency Encryption is quick however extra weak in Symmetric Encryption. | Encryption is gradual as a result of excessive computation in Uneven Encryption. |
| Algorithms- | It makes use of the algorithms akin to DES, 3DES, AES and RC4. | It makes use of the algorithms akin to Diffie-Hellman, RSA |
| Goal- | It’s primarily used for bulk information transmission. | It’s most frequently used for securely exchanging secret keys. |
11) What do you perceive by CIA triad?
CIA is an acronym that stands for Confidentiality, Integrity, and Availability. It’s generally generally known as the CIA triad. CIA is a mannequin that specifies the information insurance policies for Info Security. It is likely one of the hottest fashions utilized by organizations.
- Confidentiality: It specifies that the knowledge needs to be accessible and readable solely to approved personnel and ensures that unauthorized personnel can not entry it. The knowledge needs to be strongly encrypted in order that if somebody makes use of hacking to entry the information, they can’t learn or perceive it.
- Integrity: Integrity is used to make sure that an unauthorized entity has not modified the information. It additionally ensures that information shouldn’t be corrupted. If a certified particular person/system tries to switch the information and the modification shouldn’t be profitable, the information reversed again and shouldn’t be corrupted.
- Availability: It ensures that the information is obtainable to the consumer at any time when the consumer requires it. To attain this, sustaining {hardware}, upgrading them often, information backups and restoration are vital.
12) What’s the distinction between Encryption and Hashing? / How is Encryption completely different from Hashing?
Encryption and Hashing are methods used to transform readable information into an unreadable information format, however they’ve some key variations.
Variations between Encryption and Hashing
| Encryption | Hashing |
|---|---|
| Encryption is used to make short-term information conversions. | Hashing is used to make everlasting information conversion into message digest. |
| In Encryption, the encrypted information will be transformed again to authentic information by the method of decryption. | In Hashing, the hashed information can’t be transformed again to authentic information. |
| Encryption works in two methods, i.e. encode and decode the information. | Hashing is a one-way encryption course of. For instance, it solely encodes the information. |
| Encryption is used to safe delicate information from the attain of third events. | Hashing is used to guard the integrity of the knowledge. |
| Encryption focuses on the confidentiality of the information. | Hashing focuses on the integrity of the information. |
13) What’s the distinction between IDS and IPS?
IDS stands for Intrusion Detection System. It’s used to detect intrusions, and it warns directors to watch out whereas stopping the intrusion. IPS stands for Intrusion Prevention System, and it facilitates the system to seek out the intrusion and forestall it.
14) What are some widespread Hashing capabilities/algorithms?
Following is the checklist of some widespread and most used hashing capabilities/algorithms:
Message-Digest Algorithm (MD5)
Message-Digest Algorithm or MD5 is the newest and superior type of MD4. It was launched after discovering extreme safety points in MD4. MD5 is used to generate 128-bit outputs for a variable size of inputs.
MD5 is the superior model and the successor to MD4. It covers quite a lot of safety threats however fails to offer full information safety providers. It is likely one of the most generally used algorithms, however the principle concern with utilizing MD5 is its vulnerability and collisions.
Safe Hashing Algorithm (SHA)
Safe Hashing Algorithm, or SHA, was developed by the Nationwide Security Company. Later it was up to date repeatedly to enhance the safety flaws within the previous style. Its newest and superior model is SHA-2 that many companies are utilizing for cryptographic functions.
Tiger Cipher Algorithm
Tiger cypher algorithm is a quicker and extra environment friendly algorithm in comparison with Message Digest (MD5) and Safe Hashing Algorithm. It’s principally utilized in new era computer systems and has a 192-bit hashing system. Its newest and superior model is the Tiger2 algorithm which is extra highly effective than the Tiger algorithm.
RIPMEND Algorithm
Hans Dobbertin designed RIPMEND cryptographic hashing algorithm. It’s created utilizing the EU mission RIPE framework and has a 164-bit digest.
WHIRLPOOL Algorithm
Vincent Rijmenand Paul Barreto designed the WHIRLPOOL algorithm. It accepts any messages of a size lower than 2256 bits and returns a 512-bit message digest. Its first model was whirlpool-0, the second model was named Whirlpool-T, and the newest and most superior model is Whirlpool.
15) What’s the essential objective of Hashing?
Hashing is required when we’ve to match an enormous quantity of knowledge. We are able to create completely different hash values for various information, and we will evaluate hashes too.
Following is an inventory of some most vital utilization of Hashing:
- Hashing facilitates us to maintain and discover information of hashed information.
- Hashing can be utilized in cryptographic purposes akin to a digital signature.
- With using hashing, we will create random strings to keep away from information duplication.
- Geometric hashing is a sort of hashing utilized in pc graphics to assist discover proximity points in planes.
16) What’s a Firewall? What’s the utilization of it?
A Firewall will be outlined as a community safety system set on the boundaries of the system/community and is used to watch and management the community visitors. The principle utilization of Firewalls is to guard the system/community from viruses, worms, malware, threats and so on. Firewalls may also be used to stop distant entry and content material filtering.






Leave a Comment