17) What do you perceive by VA (Vulnerability Evaluation) and PT (Penetration Testing)?
Because the identify specifies, VA or Vulnerability Evaluation is the method of discovering vulnerabilities or flaws on the goal. On this course of, the group already is aware of that their system/community has flaws or weaknesses and desires to seek out these flaws and prioritize fixing them.
PT or Penetration Testing is the method of deep looking and discovering vulnerabilities on the goal. On this course of, the organizations arrange all of the doable safety measures they may consider and check if there may be some other method their system/community will be hacked.
18) What do you perceive by Black Hat Hackers, White Hat Hackers, and Gray Hat Hackers?
Black Hat Hackers: Black Hat Hackers are essentially the most important sorts of hackers. They try to acquire unauthorized entry to a system to disrupt its operations or steal delicate and vital information. Black Hat Hackers are also referred to as crackers.
Black Hat Hacking is at all times unlawful as a result of its malicious purpose. The principle objective of Black Hat Hacking is to steal firm information, violate privateness, trigger system harm, block community connections, and so on.
White Hat Hackers: White Hat Hackers are used to entry the system for penetration testing and vulnerability assessments. They by no means intend to hurt the system; relatively, than try to uncover holes in a pc or community system. White Hat Hackers are additionally known as Moral Hackers.
Hacking completed by White Hat Hackers is named Moral hacking. It’s not a criminal offense, and it’s thought of one of the crucial tough professions within the IT enterprise. Many companies rent moral hackers to do penetration exams and vulnerability assessments.
Gray Hat Hackers: Gray Hat Hackers are a mixture of Black Hat Hackers and White Hat Hackers. They use parts of each black and white hat hacking methods. They’re imagined to act with out malice, however for the sake of amusement, they will exploit the safety flaw in a pc system or community with out the permission or information of the proprietor.
The principle objective of Gray Hat Hackers is to attract the homeowners’ consideration to the safety flaw or gap within the community within the hope of receiving gratitude or a reward.
19) What’s Traceroute in Cyber Security?
In Cyber Security, a traceroute is used to point out the packet path by itemizing all of the factors that the packet passes by way of. Traceroute is especially used when the packet doesn’t attain the vacation spot. With the assistance of a traceroute, we will examine the place the connection breaks or stops to establish the failure.
20) What’s a VPN? What’s its use in Cyber Security?
VPN is an acronym that stands for Digital Personal Community. It creates a secure encrypted tunnel throughout the web by connecting a VPN server to a VPN consumer.
Suppose a consumer has a VPN consumer put in on their machine. The VPN consumer then creates an encrypted tunnel to the VPN server, and the consumer can securely ship or obtain data over the web.
21) What do you perceive by Brute Pressure Assault? How are you going to forestall it?
A brute Pressure Assault is a technique of discovering the suitable credentials by repetitively attempting all of the permutations and combos of doable credentials. Brute Pressure Assaults are automated normally the place the instrument/program robotically tries to log in with an inventory of doable credentials.
Following is an inventory of some methods to stop Brute Pressure Assaults:
- Password Size: The size of a password is a vital side to make it laborious to crack. You may specify to set at the very least a minimal size for the password. The lengthier the password, the tougher it’s to seek out.
- Password Complexity: You may embrace completely different character codecs within the password to make brute-force assaults tougher. Utilizing the mixture of alpha-numeric key phrases together with particular characters and higher and decrease case characters can improve the password complexity making it tough to be cracked.
- Limiting Login Makes an attempt: You can also make the password laborious for brute power assaults by setting a restrict on login failures. For instance, you possibly can set the restrict on login failures as 5. So, when there are 5 consecutive login failures, the system will prohibit the consumer from logging in for a while or ship an E mail or OTP to log within the subsequent time. As a result of brute power is an automatic course of, limiting login makes an attempt will break the brute power course of.
22) What do you perceive by Port Scanning?
Port scanning is the method directors, and hackers use to establish the open ports and providers accessible on a bunch. Hackers use this method to seek out data that may be useful to seek out flaws and exploit vulnerabilities, and directors use this method to confirm the safety insurance policies of the community. Following is an inventory of some most typical Port Scanning Strategies:
- Ping Scan
- TCP Half-Open
- TCP Join
- UDP
- Stealth Scanning
23) What’s the distinction between the Host Intrusion Detection System (HIDS) and Community Intrusion Detection System (NIDS)?
As we all know, HIDS and NIDS are each Intrusion Detection Techniques and work for a similar objective, i.e., to detect intrusions.
Distinction between HIDS and NIDS:
| Host Intrusion Detection System (HIDS) | Community Intrusion Detection System (NIDS) |
|---|---|
| HIDS is about up on a selected host/system and screens the visitors of a selected system and suspicious system actions. | Then again, NIDS is about up on a community and is used to watch the visitors of all community gadgets. |
| HIDS is used to detect intrusions. | NIDS is used for the community to watch the visitors of all gadgets. |
24) What are the several types of Cyber Security?
Each group has some property which are made up of quite a lot of completely different programs. These programs will need to have a powerful Cyber Security side to make the group work effectively. In response to the gadgets utilized in Cyber Security, it may be divided into the next varieties:
- Community safety: Community safety is likely one of the most vital sorts of Cyber safety. On this course of, we’ve to safe a pc community in opposition to unauthorized entry, intruders, assaults, disruption, and misuse utilizing {hardware} and program. This safety additionally provides an additional layer in defending a corporation’s property from each exterior and inside threats. An instance of Community safety is utilizing a Firewall.
- Software safety: Software safety is used to safeguard program and gadgets in opposition to malicious assaults. This may be achieved by often updating the apps to make sure that they’re safe in opposition to threats.
- Id administration & safety: Id administration & safety identifies every particular person’s degree of entry inside a corporation. For instance, you possibly can prohibit and enable entry to information in accordance with a person’s job position within the firm.
- Information safety: Information safety is used to make sure that you place your information in a powerful information storage system to make sure information integrity and privateness whereas in storage and transport.
- Operational safety: Operational safety is used to research and make selections about dealing with and securing the information property. For instance: Storing information in an encrypted kind within the database is an instance of Operational safety.
- Cellular safety: Cellular safety is used to specify the safety of organizational and private information held on cell gadgets akin to cell telephones, PCs, tablets, and different comparable gadgets in opposition to varied hostile assaults. Examples of cell safety threats are unauthorized entry, system loss or theft, malware, and different threats that may hurt cell gadgets.
- Cloud safety: The principle purpose of cloud safety is to safeguard the information held in a digital atmosphere or cloud infrastructures for a corporation. It makes use of varied cloud service suppliers, together with AWS, Azure, Google, and others, to guarantee safety in opposition to quite a lot of threats.
25) What do you perceive by Unicasting, Multicasting, and Broadcasting? What’s the distinction between them?
Unicasting, Multicasting, and Broadcasting are the three strategies used to transmit information over a community.
- Unicasting: Unicasting is used to ship data from a single consumer to a single receiver. This technique is used for point-to-point communications.
- Multicasting: Multicasting is used to ship information from a number of sources to a number of locations.
- Broadcasting: Broadcasting is also referred to as one-to-all. On this technique, a single sender sends the information over a number of receivers. I.e. the communication is completed between a single consumer and a number of receivers. The very best instance of broadcasting is radio or TV broadcasting, the place a single sender sends indicators to a number of receivers.
26) What are the steps used to arrange a firewall?
Following is an inventory of various steps used to arrange a firewall:
- Username/password: It’s a must to modify the default password for a firewall system, which is required to make the system safe.
- Distant administration: It’s a must to disable the characteristic of distant administration.
- Port forwarding: It’s a must to configure port forwarding accordingly to make sure purposes work correctly, akin to an internet server or FTP server.
- Disable DHCP server: When putting in a firewall on a community with an current DHCP server, it could possibly create a battle except you might have disabled the firewall’s DHCP.
- Allow Logging: It’s a must to allow logging to troubleshoot firewall points or potential assaults and perceive methods to view logs.
- Safe Insurance policies: It’s a must to set strong and safe safety insurance policies in place and be sure that the firewall is configured to implement these insurance policies.
27) What’s Patch administration in Cyber safety? How usually ought to we carry out Patch administration?
In Cyber safety, patch administration is a course of to maintain the program on computer systems and community gadgets updated and make them able to resisting low-level cyber assaults. It’s utilized in any program which is susceptible to technical vulnerabilities.
We should always carry out patch administration as quickly as it’s launched. For instance, when a patch is launched for Home windows, it needs to be utilized to all machines as quickly as doable. Similar in community gadgets, we must always apply patch administration as quickly as it’s launched. We should always comply with correct patch administration for higher safety.
28) That are the very best Patch administration instruments or program? Why are they used?
Patch administration instruments or program are used to make sure that the parts of an organization’s program and IT infrastructure are updated. The patch administration instruments work by monitoring updates of assorted program and middleware options, and then they alert customers to make vital updates or execute updates robotically.
Following is an inventory of the highest 10 greatest patch administration program or instruments:
- Atera
- NinjaRMM
- Acronis Cyber Shield Cloud
- Acronis Cyber Shield
- PDQ Deploy
- ManageEngine Patch Supervisor Plus
- Microsoft System Heart
- Automox
- SmartDeploy
- SolarWinds Patch Supervisor
29) What’s the full type of SSL? Why is it used?
The complete type of SSL is the Safe Sockets Layer. It is a know-how used to create encrypted connections between an internet server and an internet browser. SSL is used to guard the knowledge in on-line transactions and digital funds to take care of information privateness.
30) What do you perceive by a botnet?
A botnet will be outlined as a set of contaminated internet-connected gadgets, akin to servers, PCs, and cell phones. These gadgets are contaminated with malware and managed by it. The first motive of a botnet is to steal information, ship spam, launch distributed denial-of-service (DDoS) assaults, and so on. It could additionally present the consumer entry to the system and its connection.
31) What’s information leakage within the context of Cyber safety?
Within the context of Cyber safety, information leakage is an unauthorized switch of knowledge exterior of the safe community. Information leakage can happen by way of e mail, optical media, laptops, USB keys, and so on.
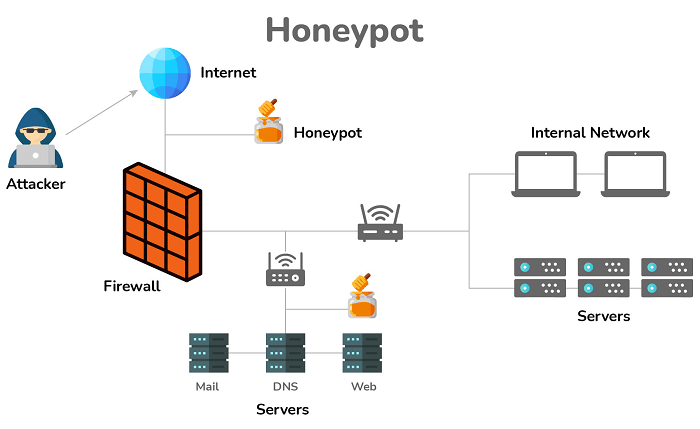
32) What do you perceive by honeypots?
Honeypots are doable assault targets set as much as see how completely different attackers try to use a community. Personal companies and governments use this idea to guage their vulnerabilities, extensively utilized in educational settings.
33) What do you perceive by Shoulder Browsing?
Shoulder browsing is a type of bodily assault utilized by fraudsters by bodily peering at folks’s screens to cheat whereas they kind delicate data in a semi-public space.
34) What are the commonest sorts of cyber safety assaults?
The commonest sorts of cyber safety assaults are:
- Malware
- Phishing
- Cross-Web site Scripting (XSS)
- Denial-of-Service (DoS)
- Area Title System Assault
- Man-in-the-Center Assaults
- SQL Injection Assault
- Session Hijacking
- Brute Pressure and so on.
35) What do you perceive by the MITM assault?
The MITM assault stands for Man-in-the-Center assault. Because the identify specifies, it’s a kind of assault the place a 3rd individual or an attacker intercepts communication between two individuals. The first intention of MITM is to entry confidential data.
36) What’s an XSS assault, and how are you going to forestall it?
The complete type of an XSS assault is a Cross-Web site Scripting assault. It’s a cyberattack that makes hackers in a position to inject malicious client-side scripts into net pages. The XSS assaults are primarily used to hijack classes, steal cookies, modify DOM, distant code execution, crash the server, and so on.
We are able to use the next practices to stop XSS assaults:
- By validating consumer inputs
- By sanitizing consumer inputs
- By encoding particular characters
- Through the use of Anti-XSS providers/instruments
- Through the use of XSS HTML Filter
37) What’s the distinction between saved XSS and mirrored XSS?
Distinction between saved XSS assaults and mirrored XSS assaults:
| Saved XSS Assaults | Mirrored XSS Assaults |
|---|---|
| The assaults the place the injected scripts are completely saved on the goal servers are referred to as saved XSS assaults. | The assaults the place the consumer has to ship the request first, then begin working on the sufferer’s browser, are referred to as mirrored XSS assaults. |
| In saved XSS assaults, the sufferer retrieves the server’s malicious script when requesting the saved data. | The mirrored XSS assaults mirror outcomes from the browser to the consumer who despatched the request. |
The article was published on December 11, 2022 @ 1:36 AM






Leave a Comment